One old saying that still holds true: “Ghar ka bhedi lanka dhaye” [Park this]. We have often heard that Anti-Virus companies are the ones who spread the viruses first & then releases an antidote for the same. Who would have thought that an Indian network security startup would plot a DDOS attack on its Indian competitor & that too using its own client’s network?
A network firm, providing Network Management systems to businesses since 2013 out of Chennai, plotted a DDOS attack on BhaiFi Networks, a 360° WiFi solution provider that provides fog-based, self-managed Network Security & Management solution to over 1500+ locations in 50 cities since 2014 out of Gurgaon.
Here is what exactly happened:
Almost 15 days back @12 Noon, we started receiving anomaly emails stating a sudden unexpected rise in Network Traffic on one of our servers. Similar emails followed just after 10 minutes & a lot more after 40 minutes. The intensity was so high that our server started acting up for a while. Since we were able to spot that it was not a normal traffic spike but an attack & within an hour we decided & shifted our entire traffic onto the failover server to avoid any downtime but we didn’t take any preventive measure at that point of time to stop the attacks on the primary server. We wanted to find out the culprit behind it. As we are already using our own Network Time Machine product for our own Network, we were able to see the attack’s intensity, trend, packet information, ports & all IP details.
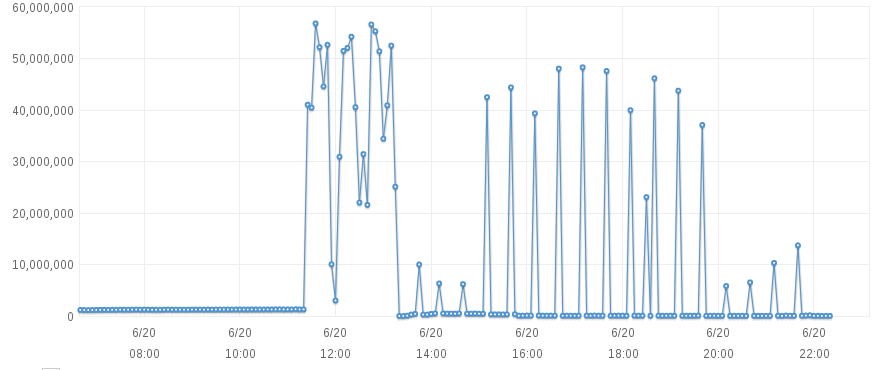

We started tracking the IPs & they were originating from:
103.84.186.7 (Delhi), 119.42.152.166 (Delhi), 173.82.10.204 (US)
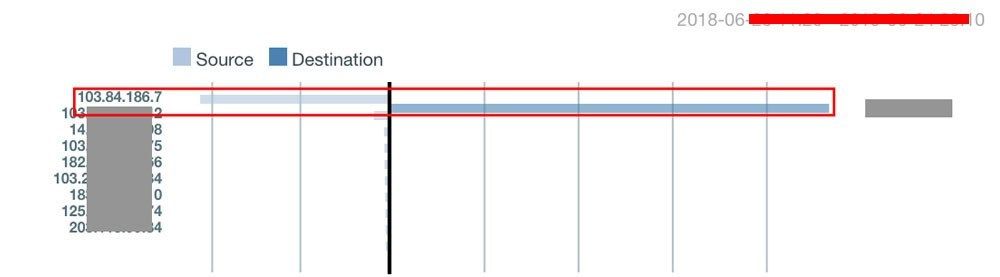
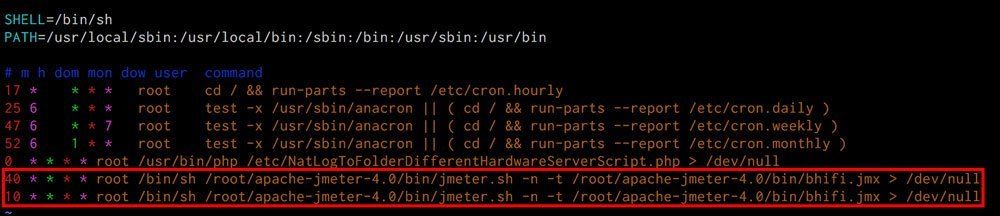
Amazingly all of them are ISPs (Internet Service Providers) themselves and such an attack needs high bandwidth & hence cannot be run from home so easily. We fetched the owner’s info & started contacting them explaining the entire scenario. Only the 1st one out of all turned up & agreed to help. He got it traced & found out that the IP was being used by him itself & it was running a server operated & managed by the above mentioned network company. We never imagined that our competitor would be involved in such misdeeds. Nevertheless, we had no evidence yet that it was done by them but it gave us enough direction. We requested the owner to give us the access to the machine in his presence to find out the crux. We logged in & found out that a CRON job was running a JMeter script scheduled to DDOS our server every 10 & 40 minutes. Script was named “bhifi.jmx” & the fake credentials used in it were quite interesting viz. fido/dido, try/now, restin/peace. We checked further & found out the same program was transferred to two other aforementioned servers through SCP.
On tracking the recent logins, we found out multiple IPs tracked to Chennai:
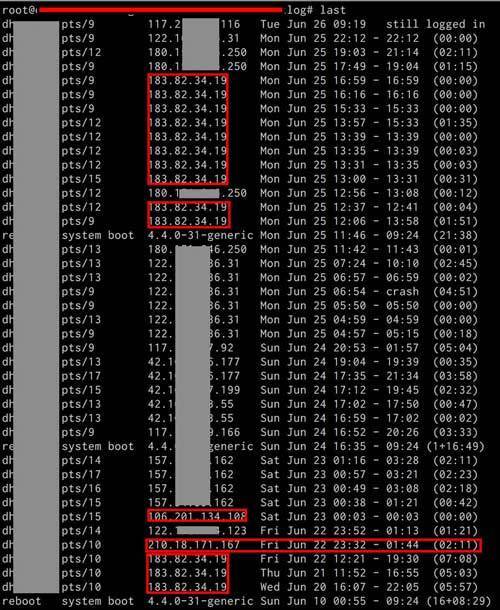
Even this was not enough for us to make sure that it was indeed a misdeed by the said company. We further scanned our logs & matched all the IPs to find out any other traces in the system & Voila! One of our own client from Chennai matched this 183.82.34.19 IP. We tracked it further & found out that a person contacted us in April ’18 from Chennai asking out for a trial to our services & he was earlier using the culprit company's solution that he was not happy with due to delayed OTP, he mentioned on the call.
He took the trial & made the payment next month.
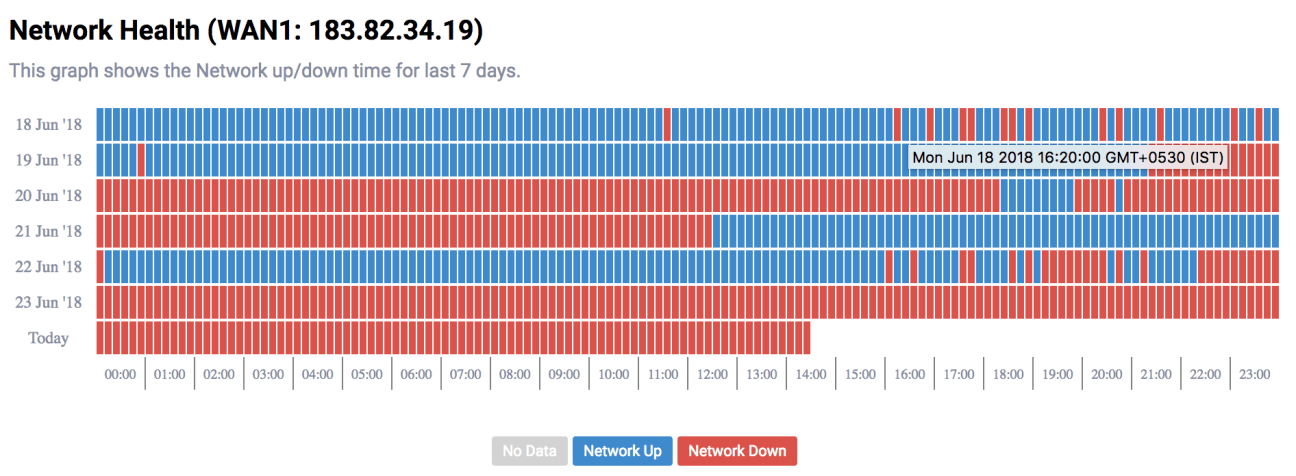
We then crawled further logs from the BhaiFi Cruze & found out that the location went down ever since the attack was started as per our Network Health Graph:
Still, it didn’t prove that Guna was from the above mentioned firm & hence we decided to list all the said company's employees on LinkedIn & that was it. His name got listed as the Network Engineer at the culprit company. Moreover and shockingly so, it was done from culprit client network, to which he could get access only being in the company.

We then decided to lodge a CyberCell complaint against this but we thought to get the system through which this attack happened & finally a week later, we were able to get the HDD in our hands & then we filed the complaint [Complaint No. C-2018/1893]. No clue how much time they are going to take but we felt the utter need of sharing this incident to all the aspiring Entrepreneurs so that they can understand the importance of the culture in a company & healthy competition that could make or break them.
We have ~25k DAU & this attack could have caused massive damage to us if we had not implemented our Failover strategies already, clubbed with our own product, Network Time Machine. We were back in action within no time.
Coming back to the old saying: “Ghar ka bhedi lanka dhaye”, if Indian startups would resort to such misdeeds within the ecosystem, how do we expect to compete globally?
Share it with your friends whom you think can be benefitted from this blog.


Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).